XIP3 - XBE Finance BUG BOUNTY – 500 000 USD Bug Bounty
This proposal is to launch the XBE Bug Bounty to reward community members for reporting bugs in the XBE protocol.
Overview
Today, we are announcing an official XBE Finance Bug Bounty Program (the ”Program”) to incentivize responsible bug disclosure.
We are offering a reward of up to $500,000 in XBE paid by the XBE Treasury.
GENERAL RULES AND GUIDELINES
- Decisions on the eligibility and size of a reward are the sole discretion of XBE Finance team and selected community members and/or auditors.
- The vulnerability must not be disclosed publicly or to any other person/s, entity, or email address before XBE Finance has been notified, has fixed the issue, and has granted permission for public disclosure. In addition, disclosure must be made within 24 hours following discovery of the vulnerability.
- Provide us with at least 5 working days to investigate the issue and respond to you.
- Any vulnerabilities should be submitted via the following contact methods: contact@xbe.finance, and/or contacting admins in the official channel Telegram.
- Issues without steps to reproduce are ineligible for the bug bounty.
- Issues must be new to the team. They can’t have already been identified by another user or by our audit.
- When possible, avoid privacy violations, degradation of user experience, disruption to production systems or data during security testing.
- No employees, contractors or others with current or prior commercial relationships with XBE Finance or any of its holding and or operating companies are eligible for rewards.
- Technical knowledge is required for the process.
- Submissions needs to be related with the Bounty Scope. Submissions out of the Bounty Scope won’t be eligible for a reward.
- Any activities conducted in a manner consistent with the rules and guidelines will be considered authorized conduct and we will not initiate legal action against you.
SCOPE
Issues which can lead to substantial loss of money, critical bugs like a broken live-ness condition or irreversible loss of funds of XBE Finance’s smart contracts, and infrastructure across all deployed chains. This includes but its not limited to Ethereum, Fantom, Avalanche, Polygon, and BSC.
EXCLUSIONS
- Already known vulnerabilities.
- Vulnerabilities in front-end code not leading to smart contract vulnerabilities and/or loss of funds.
Eligibility
- You must be the first reporter of the vulnerability
- You must be able to verify a signature from same address
- Provide enough information about the vulnerability
The following activities are prohibited by bug bounty program:
- Any testing with mainnet or public testnet contracts; all testing should be done on private testnets
- Any testing with pricing oracles or third party smart contracts
- Attempting phishing or other social engineering attacks against our employees and/or customers
- Any testing with third party systems and applications (e.g. browser extensions) as well as websites (e.g. SSO providers, advertising networks)
- Any denial of service attacks
- Automated testing of services that generates significant amounts of traffic
- Public disclosure of an unpatched vulnerability in an embargoed bounty
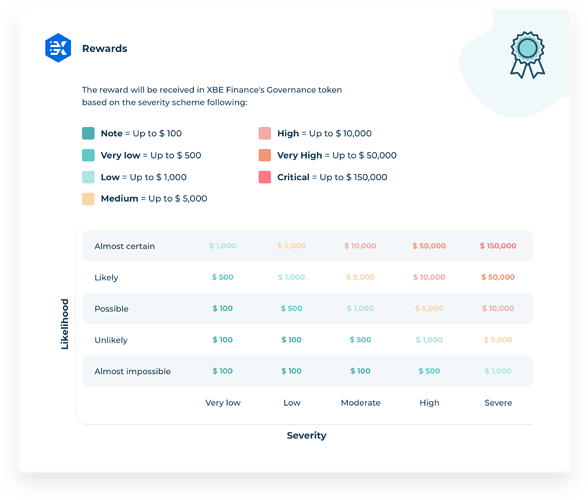
Vulnerability Ratings
Eligible rewards will be paid out of XBE treasury Wallet, at a spot rate denominated in USD at the time of payment. No KYC is required to perform this payment provided all rules are complied with.
Prioritized Vulnerabilities
We are especially interested in receiving and rewarding vulnerabilities of the following types:
Smart Contracts/Blockchain:
- Re-entrancy
- Logic errors
- including user authentication errors
Solidity/EVM details not considered
- including integer over-/under-flow
- including unhandled exceptions
Trusting trust/dependency vulnerabilities
including composability vulnerabilities
Oracle failure/manipulation
- excluding real market activity
- excluding external oracle manipulation
Novel governance attacks
Congestion and scalability
- including running out of gas
- including block stuffing
- including susceptibility to frontrunning
Consensus failures
Cryptography problems
- Signature malleability
- Susceptibility to replay attacks
- Weak randomness
- Weak encryption
Susceptibility to block timestamp manipulation
Missing access controls / unprotected internal or debugging interfaces
Web/App
- For web vulnerabilities, XBE Finance is strictly interested in those that cause direct and unequivocal loss or permanent locking of user funds
- An example would be a vulnerability that lets an attacker spoof transactions on XBE Finance web applications, leading to theft of funds
Notable mentions:
The team is further happy to allocate bounties awarded to the following members for their contribution in reporting bugs thus far.
- BDZNFT (Telegram report)
- Qiuyue (Discord report)
FOR
Vote in favour of allocating 500 000 USD (up to a maximum of 500 XBE) of XBE treasury in accordance with the above Bug Bounty
AGAINST
Vote against allocating 500 000 USD (up to a maximum of 500 XBE) of XBE Treasury in accordance with the above Bug Bounty
SNAPSHOT LINK: Snapshot
VOTE START: 19h00 CET - 10 November 2021
VOTE END: 19h00 CET - 17 November 2021